The gang talks about the Colonial Pipeline Security breach. Michael Taner and Stu Turley are joined by Connor McCarl all from the Sandstone Group. Some of the transcripts are below.
Listen to the podcast on Apple, Google, Spotify, and the Energy News Beat App in Google and the Apple store.
Podcast Automated Transcript
Michael: This is why we can still be crazy, not only do we have we wake up today and we have a merger between Bonanza Creek and extraction, which comes out of the left-field, I was called the whole time something else. I was completely wrong. You can shape it to the back half of that. I thought it was going to be maybe a Crestone extraction merger. I guess not just Bonanza Keysborough after stealing. High point. Very interesting.
Stu: Michael, you and I have been doing podcasts for about a year over a year. And that’s the first time you’ve ever been admitting to being wrong. I am stunned. I’m going to curl up in the fetal position.
Stu: Now you’re your own mentor.
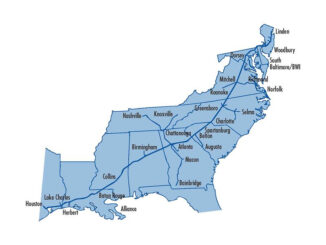
Michael, I am my own mentor. We can put that up. We need those T-shirts rolling out. I need that embroidered right underneath here. All right. So besides that, besides this merger, which normally we would spend the entire episode talking about this merger, but in light of this colonial pipeline shut down, it doesn’t even look that big. So. For those of you who have been sleeping under a rock this weekend, I know this country is opening backup concerts this weekend. I’m going to give you a quick rundown on what happened Friday. Colonial Pipeline, which is part-owned by Shell, decided to shut down its pipelines as a precaution and engaged a third-party cybersecurity firm to investigate an incident which they later confirmed was a ransomware attack. So here’s what happened. Let me see, let me pull it up here so the decision to shut the pipeline down now to give you the idea, this pipeline. Fifty-five hundred miles. It runs from Linden, New Jersey, all the way down to Houston, Lake Charles, and delivers about a little over 50 to 52 percent of the east coast of refined gasoline supply. So this is a midstream company, but this is a refined product. We’re not talking about natural gas. We’re not talking about five. This is hardcore gasoline that we could see that that supply disruptions are so close to the consumer. We’re the scary part is we could begin to see some of this stuff, soak
Stu: In the industry. They call it downstream.
Michael: So there was this company called called called Dark Side. They took about 100 gigabytes of data. But here’s the company. It was an extortion scheme. So I think why would it roll out? I think a lot of people were very scared because it’s like, holy smokes, we’ve got a ransomware attack. We’re all shut down. Well, when you dove into it, it was all business data that was stolen. And they said that they would leak all of the sensitive data to the Internet. If they did not pay the ransom and so the company decided to shut down the pipeline as a precaution in order to make sure that obviously, they did have this because there’s this huge company. But. The wild story, because this is, like I said, 50 percent of all refined products, gasoline, diesel, and jet fuel that goes to the East Coast and they haven’t said when they’re going to reopen yet. It’s still shut down. We’re talking this was late Friday afternoon to it’s now Monday. It’s a record this Monday at Central, 11:00 Central. My goodness.
Stu What, Michael, the end result is going to be horrific on this. And there’s just whenever you’re done with the details, let me know.
Michael: Yeah, it’s because I want to tee up our next guest here because. This is something that here at Sanshin, we’ve weave on top of being experts in the news field, and I leave that up to Stu stupidly. He’s the heart and soul behind. News media keeps update on that. One of the biggest things we do for clients is to help them in the technology field because we are lucky enough as a company to have a group of advisers and group people who don’t come from oil gas because I think it’s one of them, you know, get on my soapbox later. But I think one of the biggest flaws in oil and gas is that everyone who hires an oil and gas has that. It’s this one big circle. I could use a word for it, but I won’t. It’s just one big circle of people. Or having to have oil and gas experience when if you looked on the trajectory of. Industries that are developed, oil and gas are so far lagging, why? Because it’s a budget group. So with that, I’m going to bring in a board member, board adviser, and my good friend, Carl McCall, who we tap often when we engage clients in technology issues. And Connor, thank you for making your podcast debut. This is exciting.
Connor: Thank you. I appreciate it. We appreciate you, Mike and Stu, for having me on.
Stu There’s a round of applause,
Connor: so the question. So so what’s interesting? So I’ll give you a little bit of history, a history of ransomware and what it is, and then talk to you about how this dark side group, it’s not even a company. It’s a group of hackers that have come together with an objective, a mission. And it’s a little bit different than what we’ve seen in ransomware over the last probably five to 10 years. Ransomware is not new. What ransomware is now, first and foremost, I’m not a cybersecurity expert. My background is heavy I.T. software development, full-stack, and then a lot of networking over the last five years. So, you know, I’m not a cybersecurity expert. We have cybersecurity experts on untap. If you or your company is interested in cybersecurity, specifically, reach out to us and we can talk to you more. But ransomware at a high level is really just one fancy word for a type of malware. Malware is a piece of code or usually a piece of code that is distributed through systems. A lot of times phishing, email, phishing scams are popular. Right? We see those all the time where, you know, someone spoofs an email address. You are working at a big company and you get an email from your IT department, but it’s not really from your I.T. department. It’s got a link in it. You know, it says, you know, download this ransomware dotcom, accesses your Microsoft three sixty-five account. Right. And you click on it. You know, we see this all the time. I see. I saw this with one of our clients just a week, two weeks ago, actually. And it was it was. And I hear about them all the time and it community my whole network of professionals. I probably hear about ransomware attacks on large companies across industries in the industry. This seems like the most prominent oil and gas one that’s happened as of late. But this is happening all the time. So this is not new. So ransomware, right? So it’s just a piece of code. It’s malware. Technically, it’s malicious software that does something. Now, we don’t know what it does. Right.
Michael: It seems like in this case and in this case, it seemed like it was business data, but one hundred gigabytes of business data that was stolen, their internal team. And I want to make that very clear, their internal team decided we should shut the pipeline down.
Connor: Yeah, and that’s interesting because I’ll tell you, the most popular ransomware attack that’s happened the last five years was want to cry, want to cry was big ransomware that hit. And what traditional ransomware attacks do and want to cry was very similar to this, was that it takes to access. So it finds an entry point, usually through a user, and end-user. Usually, they hit you with an email, phishing email still here. Part of the old boys club doesn’t understand tech K, you know, if so,
Connor: That was true. And so an end-user will get this email or some other means. Use this via fishing email. They’ll click on the link without knowing it. They won’t see a download thing. It’ll be hidden in the background, download something to the user’s computer and then they’ll start running code. And this code usually doesn’t know things right. I Want to Cry was a very popular one, hit a lot of companies probably several years ago. It’s probably still around, I think. And what we’ll do is we’ll lock files. Very common. The ransomware attack encrypts the desktop. We’ll start localizing encrypting the desktops. You can’t access the files. And then if that user has permissions, maybe your team hasn’t done its correct job of limiting user permissions that
Michael, I got a question for Stu here, because Stu Stu is old tech. You build out tech in the oil field. Old school. Yes. Out West. Well, there are a couple of things. Okay. On a scale of terrible to bad, where does oil and gas fall within technology?
Stu Good question, Michael. And from a scale of terrible to good there, maybe 10 percent is good. The energy industry is terrible. All of our infrastructure and our complete backbone are wide open. I hate to tell anybody that’s on the hacker squad out there, but we’re wide open. We’ve been wide open for fifteen, twenty years and old school oil as using skater skates and everything else. These kinds of things were made before intelligence was out there. Like me, you know, Moses and I are buddies. So when you take a look at the encryption and everything else that was coming along around the twenty fourteen range and guess what? A lot of the oil companies were using Solarwinds and Solarwinds is Chinese. And so you sit back and go, it’s a very nice text. So Michael, does that answer your question? We are in a terrible position for security.
Connor: Can you hear me better now? My least access, control, and backups. And what I was getting to is this. When you set up a backup, check your backup, it’s not good enough to set up backups, but weekly checks. Your I.T. team needs to be doing daily, sometimes in certain environments. Right. You should have like we had sunshine in our production Pegasus Environment. We have currently five levels, different levels of backups. And we’re going to add two different levels of backups, redundant data, center backups, and other things that our current client base is now needing to. We’re going to have public plower cloud backups. We’re going to be able to restore full public live environments within forty-five minutes like that. And that’s the key. Right, because all the time when I was talking about the MSPs, I mean, you know, we in my time running that department at that company, you know, I was right out of college and I was running ahead of the software development company for a 30-year-old MSP that specialized in the apparel industry working with clients as large as Karen Kane. Three hundred million dollars, your business, well-known clients. J.Crew Long story short is this. We had a client that got hit by ransomware back up and the difference between that attack and this, what normally happens is it hits the client’s computer. It accesses as many as many resources as it possibly can and it locks down the network. And usually what happens is you can’t utilize the machine’s rights you have to pay to access it again.
Stu So when you’re sitting there corner and we’re talking about security for possibly the energy and those kinds of things, got any thoughts on what these people can do? And just saying it for energy on that?
Connor Absolutely. Yeah. And so so the really biggest thing is this. You have to have backups. You know, if you don’t have access to security controls, like with this one, we don’t know the specifics of the dark side hack by business data. You know what happened. Right. But you need backups, right? Because if they lock their system down, you know, you need us. You need to take your system offline, which is what the I.T. team probably did. Right. We got to take our shirts. You know, we got to figure out the breach. We’ve got to stop the network attack. It might be continuing to encrypt things, find where the breach is, attack it and restore from backups. Right. Or pay their fees, because that’s where a lot of these ransomware attacks now. So what companies can do, right. You have to understand that what’s really what your own you know, the key to cybersecurity is this. You’re going to get hacks who don’t talk about it. Now people talk about it’s not if it’s when. Right. It’s it might be a hundred years. It might be two hundred years, but it’s going to happen. Right. So the only sort of real recourse that you have is backups. Right. You know, and the earlier source thing is, you know, at least, you know, the two things that any company can do, any only customer today can do. This is not how this will take a week. Your I.T. teams a week to do go through your access logs. How many users you have. You have five hundred users. You got a thousand. You’ve got you got 50000 users. You’ve got one hundred thousand users globally. I don’t care. It’s not that hard. If you’re if you have one hundred thousand users, it’s on your you’re probably an actor, director of a sophisticated IT team. You have security groups. If you have 50 users, you should be in mine.
For any questions, contact Sandstone or Michael Tanner at michael@sandstonecg.com