
The Colonial Pipeline carries 2.5 million barrels a day – 45% of the East Coast’s supply of diesel, gasoline and jet fuel.
It was completely knocked offline by a cyber-criminal gang on Friday and is still working to restore service.
The emergency status enables fuel to be transported by road.
Experts say fuel prices are likely to rise 2-3% on Monday, but the impact will be far worse if it goes on for much longer.
Multiple sources have confirmed that the ransomware attack was caused by a cyber-criminal gang called DarkSide, who infiltrated Colonial’s network on Thursday and took almost 100GB of data hostage.
Colonial said it is working with law enforcement, cyber-security experts and the Department of Energy to restore service.
On Sunday evening it said that although its four mainlines remain offline, some smaller lateral lines between terminals and delivery points are now operational.
 IMAGE COPYRIGHTCOLONIAL PIPELINE
IMAGE COPYRIGHTCOLONIAL PIPELINE“Quickly after learning of the attack, Colonial proactively took certain systems offline to contain the threat. These actions temporarily halted all pipeline operations and affected some of our IT systems, which we are actively in the process of restoring,” the firm said.
“We are in the process of restoring service to other laterals and will bring our full system back online only when we believe it is safe to do so, and in full compliance with the approval of all federal regulations.”
Independent oil market analyst Gaurav Sharma told the BBC there is a lot of fuel now stranded at refineries in Texas.
The emergency amendment of the Jones Act enables oil products to be shipped in tankers up to New York, but this would not be anywhere near enough to match the pipeline’s capacity, he warned.
“Unless they sort it out by Tuesday, they’re in big trouble,” said Mr Sharma. “The first areas to be impacted would be Atlanta and Tennessee, then the domino effect goes up to New York.”
He said oil futures traders were now “scrambling” to meet demand, at a time when US inventories are declining, and demand – especially for vehicular fuels – is on the rise as consumers return to the roads and the US economy attempts to shake off the effects of the pandemic.
Ransomware as a service
While DarkSide is not the largest such gang in this space, the incident highlights the increasing risk ransomware is posing to critical national industrial infrastructure, not just businesses.
It also marks the rise of an insidious criminal IT eco-system worth tens of millions of pounds, that is unlike anything the cyber-security industry has ever seen before.
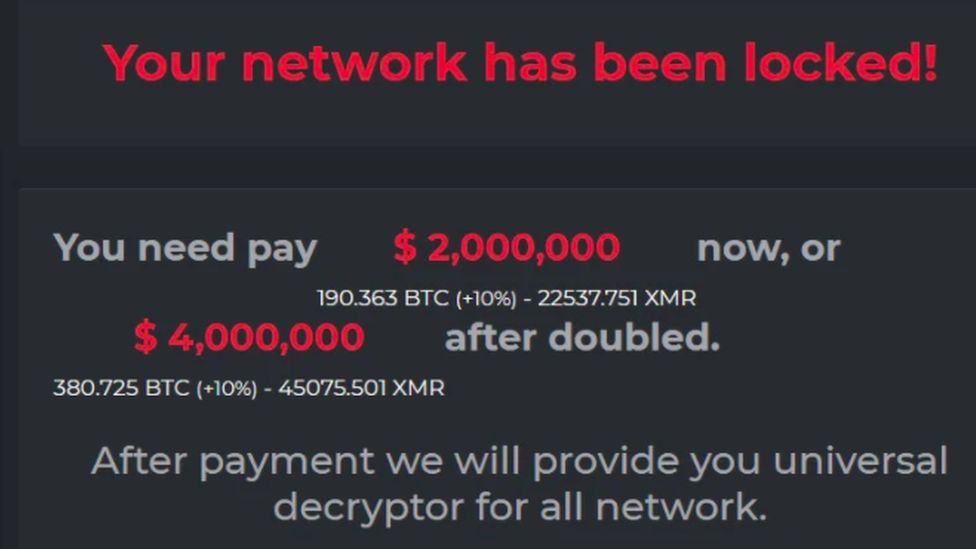
In addition to a notice on their computer screens, victims of a DarkSide attack receive an information pack informing them that their computers and servers are encrypted.
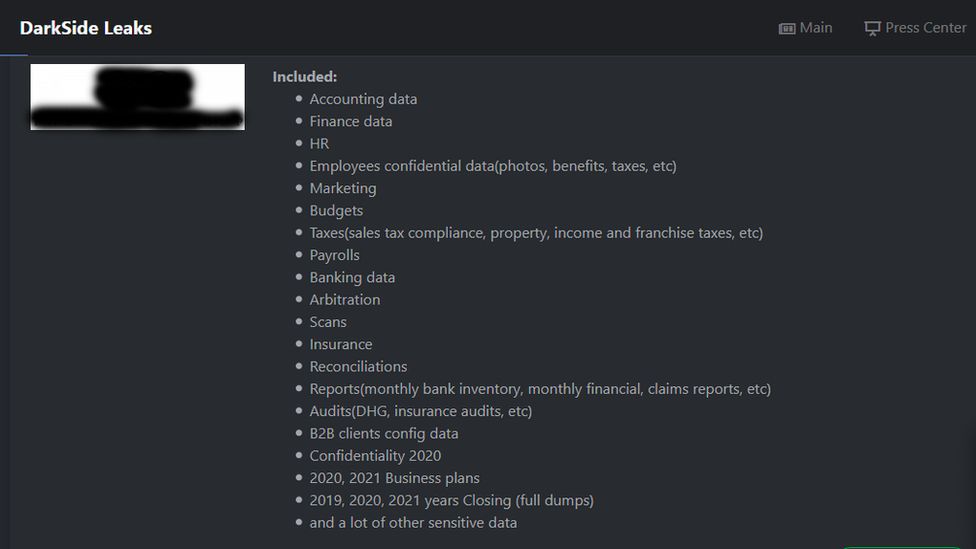
The gang lists all the types of data it has stolen, and sends victims the URL of a “personal leak page” where the data is already loaded, waiting to be automatically published, should the company or organisation not pay before the deadline is up.
DarkSide also tells victims it will provide proof of the data it has obtained, and is prepared to delete all of it from the victim’s network.
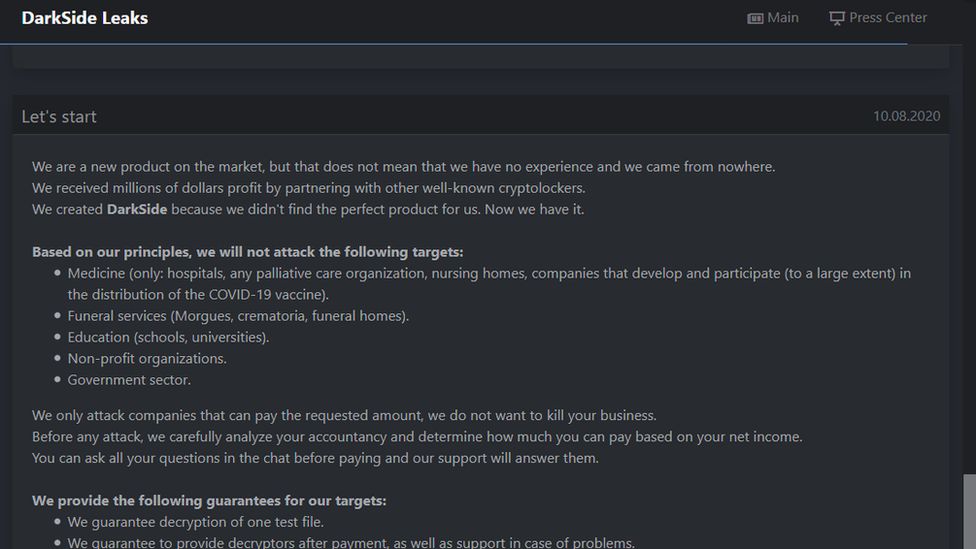
According to Digital Shadows, a London-based cyber-security firm that tracks global cyber-criminal groups to help enterprises limit their exposure online, DarkSide operates like a business.
The gang develops the software used to encrypt and steal data, then trains up “affiliates”, who receive a toolkit containing the software, a template ransomware demand email, and training on how to carry out attacks.
The affiliate cyber-criminals then pay DarkSide a percentage of their earnings from any successful ransomware attacks.
And when it released a new software in March that could encrypt data faster than before, the gang issued a press release and invited journalists to interview it.
The gang even has a website on the dark web where it brags about its work in detail, listing all the companies it has hacked and what was stolen, and an “ethics” page where it says which organisations it will not attack.
It also works with “access brokers” – nefarious hackers who work to harvest the login details for as many working user accounts on various services as they can find.
Rather than break into these accounts and alert users or the service providers, these brokers sit on the usernames and passwords and sell them off to the highest bidders – cyber-criminal gangs who want to use them to carry out much larger crimes.
How did the attack occur?
Digital Shadows thinks the Colonial Pipeline cyber-attack has come about due to the coronavirus pandemic – the rise of engineers remotely accessing control systems for the pipeline from home.
James Chappell, co-founder and chief innovation officer at Digital Shadows, believes DarkSide bought account login details relating to remote desktop software like TeamViewer and Microsoft Remote Desktop.
He says it is possible for anyone to look up the login portals for computers connected to the internet on search engines like Shodan, and then “have-a-go” hackers just keep trying usernames and passwords until they get some to work.
“We’re seeing a lot of victims now, this is seriously a big problem now,” said Mr Chappell.
“Every day there’s new victims. The amount of small businesses that are falling victim to this – it’s becoming a big problem for the economy globally.”
Mr Chappell added that Digital Shadows’ research showed the cyber-criminal gang is likely based in a Russian-speaking country, as it seems to avoid attacking companies in the Commonwealth of Independent States – an organisation of the countries of Russia, Ukraine, Belarus, Georgia, Armenia, Moldova, Azerbaijan, Kazakhstan, Kyrgyzstan, Tajikistan, Turkmenistan and Uzbekistan.



